WINDOWS 10 will be scheduled for its first major overhaul in 2019 to present a host of new features that will excite Microsoft fans. The best additions you will find in the Windows update for 10 May 2019 are listed here. Express.co.uk.
Windows 10 is the computer system used by computers all over the world by Microsoft. Typically, the software gets two updates a year –in April and October, these arrived in 2018.
This year, Windows 10 will be the first major new version known as Update May 2019, and will be published next month for each user.
Microsoft released recently the last update of the release preview cycle for Windows 10 May 2019 before the initial release.
A number of features are provided with the new giant American technology software to enhance Windows 10.
Having said that, here is a list of the best new additions from Express.co.uk.
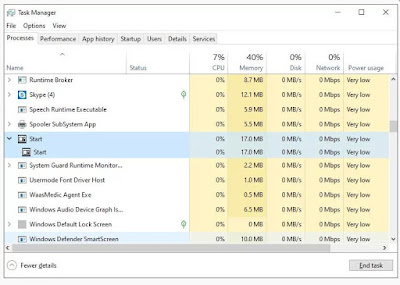
Windows Sandbox
Windows Sandbox is a new piece of
Windows 10 software that runs an remote desktop environment to test "untrusted" programs.
In principle, if an open application contain harmful materials, the idea behind Sandbox is that it will not adversely affect the device of the user.
Microsoft discussed this addition: "Windows Sandbox is a new lightweight desktop environment that's designed for safe running isolated applications.
"How many times did you download an executable file, but were afraid to run it? Have you ever been in a situation requiring clean Windows installation, but didn't want to set up a virtual machine?
"These are the situations we have regularly experienced at Microsoft and we have developed Windows Sandbox: an isolated desktop environment in which you can run unreliable software without fear of permanent impact on your device.
"Any software installed in Windows Sandbox only remains in the sandbox and cannot affect your host. Once Windows Sandbox is closed, all software with all its files and state is permanently deleted."
 |
| Windows Sandbox is one of the biggest new additions to Windows 10 |
New Start menu
According to Microsoft, the Windows 10 May 2019 update will introduce a "simplified default start layout for new devices.
" The American tech giant insisted that the signature menu will have a "one column design" that should be more accessible to fans in general.
Discussing the functionality, Microsoft said: "Based on your feedback, we are introducing a simplified default start layout for new devices, new user accounts, and clean installations.
" The new layout has been simplified into a sleek one-column design with reduced top-level tiles.
"With previous changes that provide you with the opportunity to uninstall further Inbox apps and a new way of easily unpinning a folder or group of tiles, the simplified Start layout is part of a continuous effort that improves your Start experience for the upcoming Window release."
 |
| The new Start menu will have a 'one column design' |
Search and Cortana have been separated
Search, Cortana, the new version of Windows 10, now allows users a more defined way of access.
Previously, the functionality of the virtual assistant was integrated into the search bar in Microsoft software's base panel.
But now a button has been placed for Cortana next to the box, which Microsoft said would allow both "innovative independently."
"We will be disconnecting Search and Cortana into the Task Bar," the tech company continued.
 |
Search and Cortana are separated in the May 2019 Update |
Windows 10 reserved storage
It is worth noting that the May 2019 update will reserve approximately 7 GB or more of storage so that "critical OS functions always have disk space access" according to Microsoft. It is worth noting Microsoft.
The reserved space can't be removed from Windows 10 by users.Talking about the reasoning behind the change, Microsoft commented:' We're starting with the next major update to change the way Windows 10 manages disk space.
Some disk space will be reserved for use with updates, apps, provisional files and system caches through storage process.
"Our goal is that your PC's day-to-day functioning can always be improved by ensuring critical OS functions have access to disc space.
If a user almost fills in the disk space without reserved storage, multiple Windows scenarios and application scenarios will not be reliable.
Updates, apps, temporary files and caches with reserved storage are less likely to remove valuable free space and should continue to work as expected.
 |
| windows 10 reserved storage |
Removing buggy updates
The
Windows 10 May 2019 update is able to remove buggy updates so that a PC can not boot in the correct form.
Essentially, if the software can not run normally, it will check whether any recent updates are accountable.
If so, the software will uninstall and prevent the updates from being added for 30 days. Windows 10 will also show a message saying "We have removed some newly installed updates to recover your device from startup failure"
Discussing the helpful addition Microsoft said: "Occasionally, startup failures may be due to hardware issues, file corruption, or incompatible third-party software.
 |
| Removing buggy updates win10 |
'Windows will try to diagnose and correct malfunctioning caused by disk problems, corruption of the file system, invalid registry key, or other such causes if it detects your machine cannot successfully start up.